Archive
Dynamic Queries, Stored Procedures and SQL Injections
As every one knows that Ad hoc dynamic queries are prone to SQL Injection attacks, I am not going to touch that. But there is still some confusion hanging over usage of dynamic sql with in a stored procedure. This is what I thought of blogging about.
Point 1: Using dynamic SQL with in stored procedure are prone to SQL Injection attack.
Other disadvantages of using dynamic SQL includes:
- Not readable and there for un maintainable code.
- Execution path is not saved there fore every time a stored procedure is run execution path is calculated again and again.
- But there are cases when we might need to use dynamic queries inside a stored procedure. What have to be done in this case?
- To demonstrate the sql injection attacks and to give a sample how to avoid this, I created a table named test with just one column [name].
Table Definition
USE [ASPNETDEV]
GO
/****** Object: Table [dbo].[test1] Script Date: 10/28/2009 15:14:07 ******/
SET ANSI_NULLS ON
GO
SET QUOTED_IDENTIFIER ON
GO
CREATE TABLE [dbo].[test](
[name] [nchar](10) COLLATE SQL_Latin1_General_CP1_CI_AS NULL
) ON [PRIMARY]
Insert the below values in to the table.
insert into test values (‘muthu’);
insert into test values (‘muthu1’);
Case 1: Procedure using static query
create procedure testsi
(@name nvarchar(10))
as
select * from test where [name]=@name
when we execute the above procedure with normal parameters (‘muthu’) it brings just 1 row.
exec testsi ‘muthu’
Now I give a value that introduces SQL injection as below
exec testsi ‘muthu”;drop table test;–”select * from test;’
When you look in to the value passed to the parameter @name ; you can very well see the SQL injection in the form of ‘’;drop table test;—. As you see, this just closes the single quote and drops the table test. Well this is sql injection.
But to our surprise executing this does not drop the table and promptly brings in one row.
muthu
Because what we passed is just a value for the column [name] and obviously we don’t have any row in the table [test] with the column [name] having value ‘muthu”;drop table test;–”select * from test;’
Case 2: Procedure with dynamic Query
create procedure testsid
(@name nvarchar(1000))
as
declare @sql as nvarchar(1000)
set @sql=’select * from test where [name]=”’ + @name + ””
print @sql
execute (@sql)
The line given in bold is the place where we use dynamic query.
Now lets execute this procedure using our SQL Injection value.
exec testsid ‘muthu”;drop table test;–”select * from test;’
Opps! Now the table is lost.
when you see the “Messages” tab in the Management Studio to your surprise it will be as follows:
select * from test where [name]=’muthu’;drop table test;–‘select * from test;’
(1 row(s) affected)
When you separate the statement using semicolon you will get 2 statements as follows; never mind the third one is commented.
- select * from test where [name]=’muthu’;
- drop table test;
- –‘select * from test;’
So this is SQL injection and this doesn’t just disappear if you use stored procedure.
Case 3: Procedure with dynamic query and avoiding SQL injection
However Microsoft has introduced a new way to run dynamic queries from the stored procedure using sp_executesql.
From MSDN:
To execute a string, we recommend that you use the sp_executesql stored procedure instead of the EXECUTE statement. Because this stored procedure supports parameter substitution, sp_executesql is more versatile than EXECUTE; and because sp_executesql generates execution plans that are more likely to be reused by SQL Server, sp_executesql is more efficient than EXECUTE.
Please refer to the SQL server 2008 books online to get more information about this sp_executesql.
alter procedure testside
(@name nvarchar(1000))
as
declare @sql as nvarchar(1000)
declare @ParamDefinition nvarchar(500)
set @ParamDefinition = N’@name nvarchar(1000)’
set @sql=’select * from test where [name]=@name’exec sp_executesql @sql, @ParamDefinition,@name
print @sql
In the above procedure we create a dynamic parameterized query and we pass the query, the parameter definition and the value for the parameter to sp_excutesql procedure.
exec testside ‘muthu”;drop table test;–”select * from test;’
Even though we run the procedure with SQL Injection values to our surprise the table test does not get dropped.
But remember just using sp_executesql will not avoid sql injection attacks. It must be used sensibly. For example an example as follows is still susceptible to sql injection.
How not to use sp_executesql?
create procedure testsides
(@name nvarchar(1000))
as
declare @sql as nvarchar(1000)
declare @ParamDefinition nvarchar(500)
set @ParamDefinition = N’@name nvarchar(1000)’
set @sql=’select * from test where [name]=”’ + @name + ””
exec sp_executesql @sql, @ParamDefinition,@nameprint @sql
Even though the procedure uses “sp_executesql” it is still prone to SQL injection because it does not use parameterized query.
But there are times when one cannot use parameterized queries, in this case there is no way but to use dynamic query. But in this case one must take extra-ordinary steps to validate the data. This article may help further understanding.
Update:
A live example for sql injection attack: Barackobama.com!
Moving ASP.NET web application from 32 bit to 64 bit
Before we jump in to the details, we need to know few things to understand some basics.
Managed module is a standard 32 bit Microsoft Windows Portable Executable (PE32) file or standard 64 bit Microsoft Windows Portable Executable file (PE32+) that requires CLR to execute.
Parts of managed module:
| PE32 or PE32+ header |
Contains information about |
| CLR header |
This includes information about |
| Metadata |
Usually this part contains 2 tables |
| Intermediate Language code |
Code produced by compiler during compilation. At run time CLR compiles the IL in to native CPU instructions. |
Always keep in mind that all CLR complaint compilers produce IL code. At times this IL code is referred as managed code because it is managed by CLR.
| Assembly | Assembly is a logical group of one or mode modules |
| Manifest | Manifest is a set of metadata tables that have information about list of files in the assembly, the dependencies of the files in the assembly and resource or data files associated with the files |
Before we understand how CLR loads the managed code or assembly we need to study the difference between 32 bit and 64 bit versions of windows.
If your assembly files contain only type-safe managed code, you are writing code that should work on both 32-bit and 64-bit versions of Windows. No source code changes are required for your code to run on either version of Windows. In fact, the resulting EXE/DLL file produced by the compiler will run on 32-bit Windows as well as the x64 and IA64 versions of 64-bit Windows! In other words, the one file will run on any machine that has a version of the .NET Framework installed on it.
On extremely rare occasions, developers want to write code that works only on a specific version of Windows. Developers might do this when using unsafe code or when interoperating with unmanaged code that is targeted to a specific CPU architecture.
What is Unsafe Code?
http://msdn.microsoft.com/en-us/library/62bwd2yd(VS.80).aspxBy default Microsoft’s C# compiler produces safe code. Safe code is code that is verifiably safe. However it is possible to write unsafe code. Unsafe code is allowed to work directly with memory addresses and can manipulate bytes at these addresses. This is a powerful feature and is useful when interoperating with unmanaged code.
How to check if an assembly is type safe or not?
Microsoft supplies a utility called PEVerify.exe that analyses and reports the error if any unsafe code is used in the assembly.
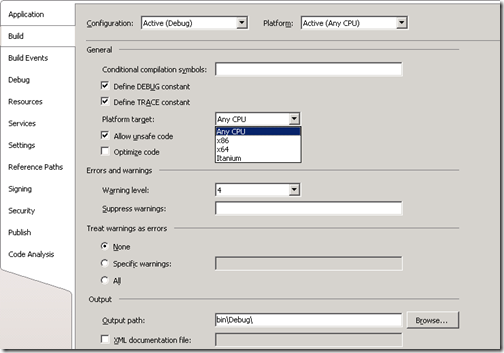
To aid these developers,the C# compiler offers a /platform command-line switch. This switch allows you to specify whether the resulting assembly can run on x86 machines running 32-bit Windows versions only, x64 machines running 64-bit Windows only, or Intel Itanium machines running 64-bit Windows only. If you don’t specify a platform, the default is anycpu, which indicates that the resulting assembly can run on any version of Windows.
Depending on the platform switch, the C# compiler will emit an assembly that contains either a PE32 or PE32+ header, and the compiler will also emit the desired CPU architecture (or agnostic) into the header as well. Microsoft ships two command-line utilities, DumpBin.exe and CorFlags.exe, which you can use to examine the header information emitted in a managed module by the compiler.
How to find Platform dependency?
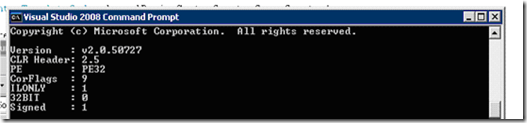
CLR Header 2.0 = .NET 1.0 or 1.1
2.5 = .NET 2.0PE PE header type
PE32 = 32-bit
PE32+ = 64-bitCorFlags Different flags ILONLY Since assembly also allowed to contain native code, to be “AnyCPU” the assembly shall contain only IL. 32BIT 1 = x86 target
0 = Any CPU targetSigned Signed 1 = Assembly signed
0 = Assembly not signedIn our example we will have to look at three properties to find if the assembly is platform dependent or not.
ILONLY –> 1
Even the assembly has only ILCode still it can be platform dependent. PE and 32 Bit properties help to get more information.
PE & 32 Bit –> PE32 & 0The combination of PE & 32 bit for different platforms are as follows:
PE 32Bit AnyCPU PE32 0 X86 PE32 1 x64 PE32(+) 0 So from the information displayed by CorFlags, our test assembly is truly “AnyCPU”
Also CorFlags can be used to forcefully change the PE headers. But personally I don’t like this because if it is compiled like that then it is done for a reason.
What happens during running of the executable?
1. Windows examines the EXE file’s header to determine whether the application requires a 32 bit or 64 bit address space
2. A file with PE32 header can run with a 32 bit or 64 bit address space
3. A file with PE32+ header requires a 64 bit address space
4. Windows also checks the CPU architecture information embedded inside the header to ensure that it matches the CPU type in computer.
WOW64
64 bit versions of windows offer a technology that allows 32 bit windows applications to run. This technology is called WOW64 (for windows on Windows 64).It would be more appropriate if it was named as ‘Windows 32 on Windows 64”. To make it simple, WOW64 acts as a layer and let 32 bit process to run as if they are running in 32 bit system even though in real they are running in 64 bit OS. As you see there is an extra cost here. There is no free lunch.The even allows 32 bit applications with x86 native code in them to run on an Itanium machine, because WOW technology can emulate X86 instruction set, but with a performance cost.
How do we know if the application is running under WOW64?
In the task manager if you see *32 near to your image name then your application is running under 32 bit emulation mode using WOW64. If you want to determine it from out of process use IsWow64Process.Also you could use Module.GetPEKind to determine the platform targeted by the module.
|
/platform |
Resulting managed module | X86 Windows | X64 Windows | IA64 Windows |
| anycpu | PE32/platform agnostic | Runs as a 32 bit application | Runs as 64 bit application | Runs as a 64 bit applications |
| X86 | PE32/X86 | Runs as a 32 bit application | Runs as a WoW64 application | Runs as a WoW64 application |
| X64 | PE32+/X64 | Doesn’t run | Runs as a 64 bit application | Doesn’t run |
| Itanium | PE32+/Itanium | Doesn’t run | Doesn’t run | Runs as a 64 bit application |
Where to set the /platform switch in VS
Process of creating a Process
After Windows has examined the EXE file’s header to determine whether to create a 32-bit process, a 64-bit process, or a WoW64 process, Windows loads the x86, x64, or IA64 version of MSCorEE.dll into the process’s address space. On an x86 version of Windows, the x86 version of MSCorEE.dll can be found in the C:\Windows\System32 directory. On an x64 or IA64 version of Windows, the x86 version of MSCorEE.dll can be found in the C:\Windows\SysWow64 directory, whereas the 64-bit version (x64 or IA64) can be found in the C:\Windows\System32 directory (for backward compatibility reasons). Then, the process’ primary thread calls a method defined inside MSCorEE.dll. This method initializes the CLR, loads the EXE assembly, and then calls its entry point method (Main). At this point, the managed application is up and running.
So,
1. If your application has only managed code then you don’t hesitate to use “Any CPU”. Best option if you are just using pure c#.
2. If your application (or any of the third party dlls) has direct native code or have an assembly that is targeted to x86 (32) then you cannot run your application in X64 environment because when the dependent assembly (targeted to x86) could not be loaded in x64 environment (will throw bad format exception). In this case, use CorFlags tool to change the target to x64, if you are so sure that can be done!. Otherwise there is a hack.
3. If any of your code targets specifically x86 platform then you must compile targeting the platform x86. This will run in x64 in emulated mode (WoW64) but bear in mind that you have a performance hit in WoW64.
4. If any of your code targets specifically x64 platform (this wont occur normally until you have specific pointer sizes) then you got no choice except to compile your application targeting X64.
First Look : ASP.NET 4 Beta 2 and Ajax Preview 4.0
I have just finished reading this white paper. I haven’t tried most of the things; but I wish to list some features which attracted me.
I can see extensive changes in AJAX but apart from that there are some remarkable changes that would give us more control by letting us extend them. As Dino Esposito says changes in ASP.NET 4.0 can be tagged as “More Control”.
The features I like in ASP.NET 4.0 Beta 2:
Core Services
Auto-Start web application:
A new scalability feature named auto-start that directly addresses this scenario is available when ASP.NET 4 runs on IIS 7.5 on Windows Server 2008 R2. The auto-start feature provides a controlled approach for starting up an application pool, initializing an ASP.NET application, and then accepting HTTP requests.
Permanently redirecting a page:
ASP.NET 4 adds a new RedirectPermanent helper method that makes it easy to issue HTTP 301 Moved Permanently responses rather than issuing HTTP 302 Found (Temporarily redirected) response which requires another round trip to the server.
Expanding the range of allowable URLs:
length of URL is no more limited to 260 and can customize the set of valid characters using the new requestPathInvalidChars attribute of the httpRuntime configuration element
Compress Session State:
When the compressionEnabled configuration option shown in the following example is set to true, ASP.NET will compress (and decompress) serialized session state by using the .NET Framework System.IO.Compression.GZipStream class. This is available only when out-of-process session is used.
Do you know it is possible to compress for in-proc session storage scenario also – even in ASP.NET 2.0?
Object Caching and Extensibility:
To make caching available for all applications, the .NET Framework 4 introduces a new assembly, a new namespace, some base types, and a concrete caching implementation. The new System.Runtime.Caching.dll assembly contains a new caching API in the System.Runtime.Caching namespace. The namespace contains two core sets of classes:
• Abstract types that provide the foundation for building any type of custom cache implementation.
• A concrete in-memory object cache implementation (the System.Runtime.Caching.MemoryCache class).
Extensible request validation:
The request validation feature has been made extensible so that we can use custom request-validation logic.(ASP.NET request validation searches incoming HTTP request data for strings that are commonly used in cross-site scripting (XSS) attacks)
AJAX 4
Client Template rendering:
Templates offer the most manageable way of creating UI from data.
The following example shows a typical client template that we can create using ASP.NET AJAX 4.
<ul id="myTemplate" class="sys-template"
sys:attach="dataview"
>
<li>
<h3>{{ Name }}</h3>
<div>{{ Description }}</div>
</li>
</ul>
Data binding
One way live binding is what we saw in previous example {{ Description }}.
Two way live binding is useful when a text box is provided that enables users to modify the value of underlying data, as in the following example:
<input type="text" value="{binding Name}"/>
In two-way live binding, the binding works in both directions. If the target value is changed (in this case, the value in the UI), the source value is automatically updated (in this case, the underlying data item). Similarly, if the source value is changed (in this case, if the underlying data value is updated externally), the target value (the value in the UI) is updated in response. As a result, target and source are always in sync.
Observer Pattern
The observer pattern enables an object to be notified about changes that occur in another object. (The term observer pattern is often misused in JavaScript frameworks to describe event handling based on the addHandler method and similar techniques.) ASP.NET AJAX 4 implements the pattern completely. It adds observer functionality to ordinary JavaScript objects or arrays so that they raise change notifications when they are modified through the Sys.Observer interface
Client side controls
The DataView control can bind to any JavaScript object or array, or to any ASP.NET AJAX component
An example:
<ul sys:attach="dataview" class="sys-template"
dataview:data="{{ imagesArray }}"
>
<li>
<h3>{{ Name }}</h3>
<div>{{ Description }}</div>
</li>
</ul>
End-to-end Ajax-based data scenarios:
The AdoNetServiceProxy class enables read-write interaction with ADO.NET Data Services from JavaScript. The class enables access from JavaScript to a broad range of features of ADO.NET Data Services.
The AdoNetServiceProxy class is used by the AdoNetDataContext class in read-write scenarios that provides full support for change tracking in the browser. This enables complete end-to-end AJAX-based data scenarios.
The following example shows how to use the DataContext class.
<script type="text/javascript">
var dataContext = new Sys.Data.DataContext();
dataContext.set_serviceUri("../Services/imagesService.svc");
dataContext.set_saveOperation("SaveImages");
dataContext.initialize();
</script><button onclick="dataContext.saveChanges()" class="right">Save Changes</button>
<ul sys:attach="dataview" class="sys-template"
dataview:dataprovider="{{ dataContext }}"
dataview:query="GetImages"
>
<li>
<input type="text" value="{binding Name}"/><br/>
<input type="text" value="{binding Description}"/>
</li>
</ul>
Web Form
View state enable/disable for individual controls:
All server controls have EnableViewState property including page. But one must remember that EnableViewState property is ignored for child controls. For example if Page has EnableViewState set to True, its child control TextBox control will always read and write to the session state no matter what we set for enableviewstate property for that control.
But ASP.NET 4.0 will change this behavior by using a special property named ViewStateMode that accepts 3 values: enabled|disabled|inherit.
This is a good improvement.
Browser capabilities:
ASP.NET 4 includes a feature referred to as browser capabilities providers. As the name suggests, this lets us build a provider that in turn lets us to use our own code to determine browser capabilities.
Routing
ASP.NET 4 adds built-in support for using routing with Web Forms. Routing lets us configure an application to accept request URLs that do not map to physical files. Instead, we can use routing to define URLs that are meaningful to users and that can help with search-engine optimization (SEO) for our application. For example, the URL for a page that displays product categories in an existing application might look like the following example:
http://website/products.aspx?categoryid=12
By using routing, we can configure the application to accept the following URL to render the same information:
http://website/products/software
Client ID creation
The new ClientIDMode property addresses a long-standing issue in ASP.NET, namely how controls create the id attribute for elements that they render.
The new ClientIDMode property lets you specify more precisely how the client ID is generated for controls. You can set the ClientIDMode property for any control, including for the page. Possible settings are the following:
• AutoID – This is equivalent to the algorithm for generating ClientID property values that was used in earlier versions of ASP.NET.
• Static – This specifies that the ClientID value will be the same as the ID without concatenating the IDs of parent naming containers. This can be useful in Web user controls. Because a Web user control can be located on different pages and in different container controls, it can be difficult to write client script for controls that use the AutoID algorithm because you cannot predict what the ID values will be.
• Predictable – This option is primarily for use in data controls that use repeating templates. It concatenates the ID properties of the control’s naming containers, but generated ClientID values do not contain strings like "ctlxxx". This setting works in conjunction with the ClientIDRowSuffix property of the control. You set the ClientIDRowSuffix property to the name of a data field, and the value of that field is used as the suffix for the generated ClientID value. Typically you would use the primary key of a data record as the ClientIDRowSuffix value.
• Inherit – This setting is the default behavior for controls; it specifies that a control’s ID generation is the same as its parent.
Query Extender – Filtering
To make data source filtering easier, a new QueryExtender control has been added in ASP.NET 4. This control can be added to EntityDataSource or LinqDataSource controls in order to filter the data returned by these controls. Because the QueryExtender control relies on LINQ, the filter is applied on the database server before the data is sent to the page, which results in very efficient operations.
The QueryExtender control supports a variety of filter options: Search,Range,Property Expression and CustomExpression.
More updates when I really work on them. Notify me incase if I had overlooked an important feature.
Happy learning!
VS2008 Tips : Organize Usings
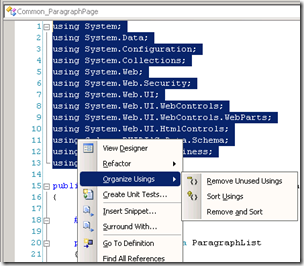
This was helpful for me manytimes and yet I have seen many developers who are not aware of this feature.
Select the using statements and right click and select Organize usings. There are 3 options available: Remove Unused Usings, Sort Usings and Remove and Sort usings.
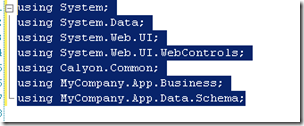
After selecting “Remove and Sort Usings” my using statements got reduced to just 7.
Simple and nice feature, right?
“Google”lable and “Bing”able Twitter
Google has reached an agreement with Twitter to include its updates in their search results. And Bing has also done the same kind of arrangements. This is a boost for Twitter and a very good news for us.
Only yesterday I wanted to search a blog post that was recommended by ScottGu. I didn’t remember the URL for the recommended blogpost. I know the words “Top 10 features asp.net 4”. The company that I work for, has banned Twitter. I thought of a search service for Twitter provided by other search giants will be good. So now it is available.
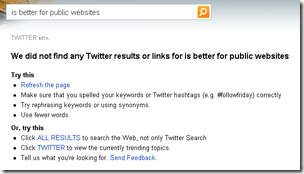
I still don’t know how to use Google to search Twitter messages but Bing has already provided an interface to search the Tweets.
But searching for this tweet didn’t bring up any results.
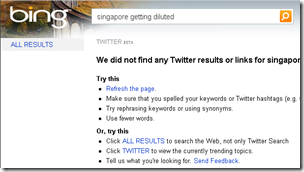
I tried to search by last tweet: Singapore getting diluted. But no luck. Bing didn’t bring up any results either.
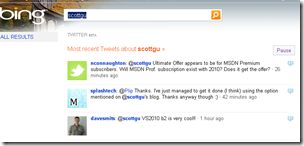
But a search on @ScottGu gave few results.
As I can see, these are the results on tweets about scottgu.
Finally I searched using Twitter search itself. And also my tweet on Singapore getting diluted. Aha! The results are just fine. Hope the twitter search from Bing and Google will be OK very soon.
API for Wolfram Alpha
now what? Wolfram Alpha is releasing its API today. The API documentation will be available at http://products.wolframalpha.com/api.
I am particularly interested in this because an API for an engine that searches and computes data might be very helpful at times. The possibilities for applications could be endless. We just need imagination.
I cannot wait to mess up with the API.
A simple search with term “uncertainity principle” gave me nice results, rather than giving me a link to a page that has the data.
I told you, you just need imagination!
Critical October Security patches
Microsoft today released a huge security patch. This includes 13 fixes out of which 6 updates are given as critical and they have the highest priority.
As we see in the priority list given by Microsoft, half of the security patches has something to do with day to day activities of the users or at worst at the server level.
As a web developer I am really concerned about patches for Internet Explorer, .Net CLR and Silver light. As a normal user the patch for Media Runtime and Media Player interests me, because I download loads of media content.
Below are the critical patches as recommended by Microsoft.
|
Vulnerabilities in Windows Media Runtime Could Allow Remote Code Execution (975682) |
|
|
Vulnerabilities in SMBv2 Could Allow Remote Code Execution (975517) |
|
|
Cumulative Security Update for Internet Explorer (974455) |
|
|
Vulnerabilities in the Microsoft .NET Common Language Runtime Could Allow Remote Code Execution (974378) |
|
|
Vulnerabilities in GDI+ Could Allow Remote Code Execution (957488) |
|
|
Vulnerability in Windows Media Player Could Allow Remote Code Execution (974112) |
Also to check for the missing security updates and misconfigurations we can use Microsoft Baseline Security Analyzer.
For MS09-061 the current vulnerabilities are explained here as follows:
- The first issue results from the manner in which Microsoft .NET verifiable code is verified, which could allow attackers to obtain a managed pointer to stack memory that is no longer used, leading to arbitrary code execution.
- The second vulnerability results from the manner in which Microsoft .NET verifiable code is verified, which could allow attackers to bypass a type equality check and execute arbitrary code.
- The third issue results from the manner in which the Microsoft .NET Common Language Runtime (CLR) handles interfaces, which could allow attackers to execute arbitrary code via a malicious application.
Amazon’s way of disabling controls
Today I saw an interesting way to disable the button shown in the web UI. Today I was browsing Amazon and trying to pre-order a book named “Confessions of the public speaker” written by Scott Berkun. I haven’t ordered books from Amazon since I have moved to this new address.
But Amazon has a validation before completing your shopping cart check out. That is: If you are shipping to a new address for the first time, you must key in your payment information again. This is for verification of authentication.
But I saw a “continue” button in the upper right corner of the screen.
I tried to click the “Continue “ button, but once I move my mouse over this button the button got faded out and ah ha, there popped a clear message explaining why I cannot click this button, at this point of time.
Rather than hiding the controls and startling the users by making them visible suddenly, this approach is cool. This is better than the approach of enable/disable controls too, for this shows a friendly message to the users; rather than showing dumb disabled control.
Nice transparent way to control the UI flow. I am thinking of writing an user control for this. 🙂
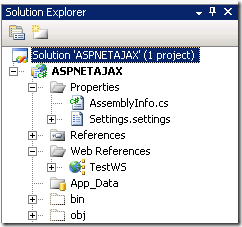
Unable to see Solution File in Solution Explorer : VS Tip
Today one of my colleagues called me for a very important (and common) doubt: He is unable to see the solution icon in the solution explorer window in Visual Studio 2008.
ASPNETAJAX is his project file and he has a solution file of the same name (ASPNETAJAX.sln). He wanted to add an existing project to this solution file, but unfortunately how hard he tried he was unable to see the solution file in the solution explorer window.
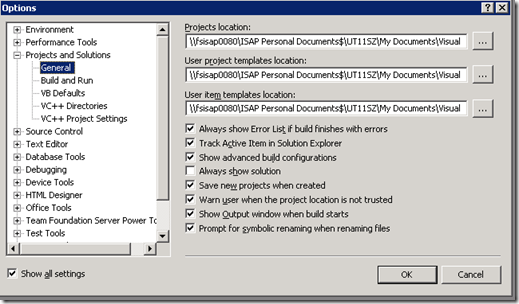
In Visual Studio 2008 everything is configurable, every time when there is a problem like this one must consult not Google but Tools –> Options menu.
Ah, there he is! Under Projects and Solutions –> General there is an option Always show solution.
If this is not enabled, when your solution file has only one project, the solution icon will not show up in the solution explorer. But if your solution file has more than one project solution file will show up always in the solution explorer, no matter whether you enable or disable this option.
After my colleague enabled this option, solution file appeared in his solution explorer.
Also find loads of visual studio tips here in Saraford’s bog. In fact all of her tips are condensed in to a lovable book.
Don’t kick your users away
Running a service website and making it successful is always tough. And that’s why only very few of sites become smash hits while some remain as mediocre for ages and get faded away. When you compare the hit sites with mediocre site, the only difference we would always see is USABILITY coupled with SIMPLENESS.
Forget usability, some site drive away people right from the registration page. Today I thought of placing an advertisement about transferring my JTC. I placed this advertisement with some sites that offer to post free advertisements. I am OK with some sites, even though they required me to get registered at first and showed unclear clumsy highly RSA “look” encrypted Word Verification. But there was one particular site (88DB) and that annoyed and drove me crazy.
See I was there to quickly post an advertisement. If I have to register myself by giving my email-id just in case for verification, I am perfectly alright. But why in the world are you asking me to fill in really un necessary information like age, salary, education etc? And these fields are mandatory. Every time I click register the site was continuously coming up with an error message asking me to fill in some unwanted detail. And there is another laughable mandatory field: what are the services you are interested in? (with numerous check boxes). Really are you aware of current trends in web design and user interaction?
Congratulations! Just now you have kicked a customer out and away from your site.
Ask little from user. Get him hooked in. Show some of your interesting stuff. Let him play and let him get a hang of your site. If he likes you, he gives other information. Do not push the user unless you run the site just for fun.











Recent Comments